Introduction
When you load a login page, you might think you're seeing just a simple form asking for a username and password. But in modern web applications - especially Single Page Applications (SPAs) - the login page is often just the tip of the iceberg.
The Problem: Login Pages Aren't Security Boundaries
Many developers forget that the browser loads most of the app's scripts even on the login screen. That means while users see a form, the entire JavaScript bundle (which might include sensitive information) is already sitting in their browser - ready for inspection.
This creates a hidden risk:
- ✅ API keys hardcoded into JavaScript
- ✅ Internal service URLs or IP addresses
- ✅ Developer emails or environment variables
- ✅ Third-party keys that should be private
Attackers know this and routinely scrape login pages looking for these kinds of exposed secrets.
How to Detect Secrets on Login Pages
Manual scanning can be annoying. That's why I built secrets.tools - a tool that:
- ✅ Loads a login page
- ✅ Crawls all accessible scripts
- ✅ Automatically scans for API keys, URLs, IPs, and emails
You can try it here: https://secrets.tools
Here is an example of a login page that was analyzed using the tool:
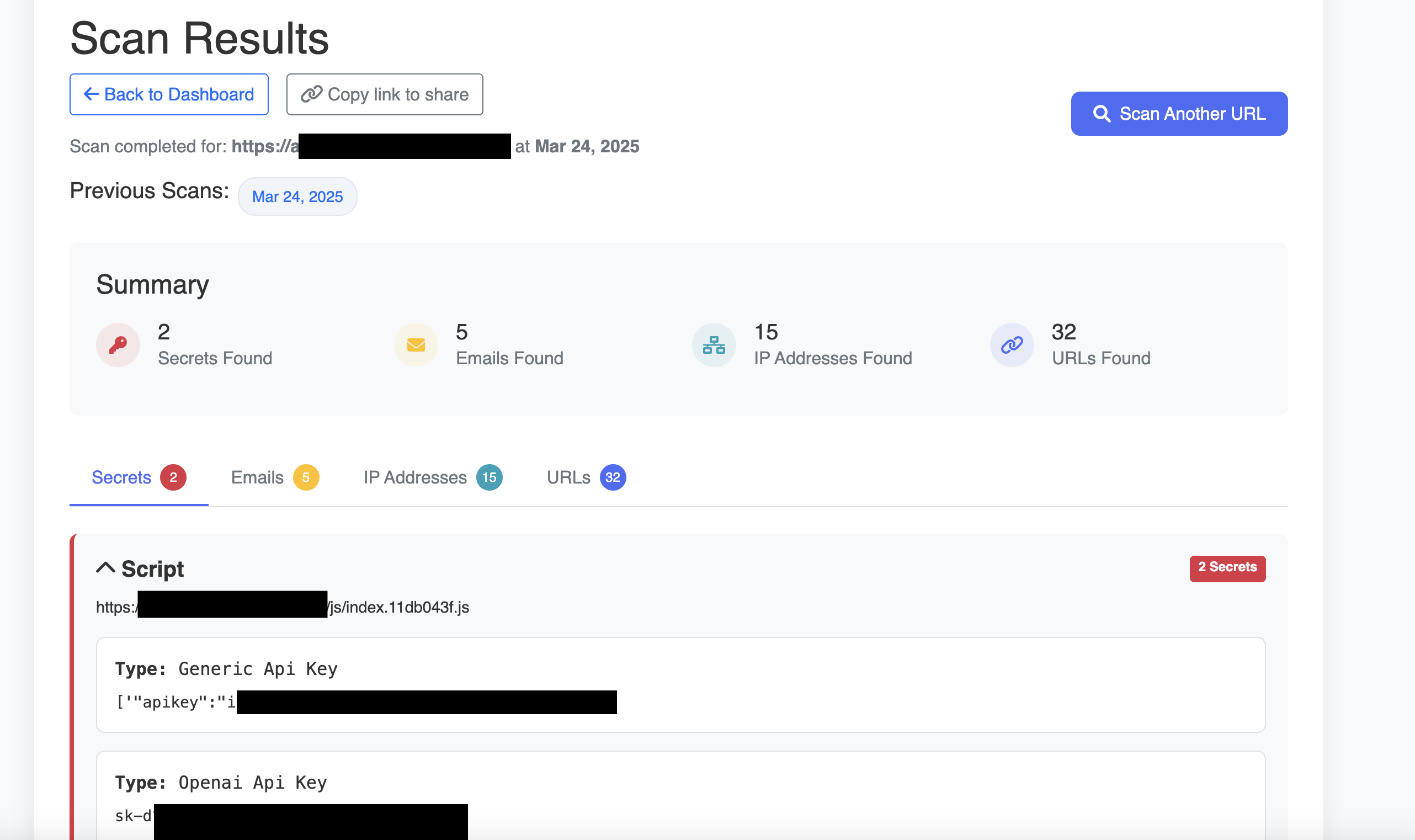
Open AI and Generatic API keys discovered in a login page
Conclusion
Exposing secrets in frontend code is a silent risk - it won't show up in a typical bug bounty test or pen test unless someone looks manually. But once exposed, API keys can be used immediately.
Here's what you can do to better protect a web application:
- Keep secrets server-side
- Use environment variables properly in your build process
- Regularly scan your production app for exposed secrets
Remember: Login pages don't protect your frontend code - they just hide it behind a form.
Need Help?
If you encounter any issues or need technical support, contact us at [email protected]